As you venture deeper into AWS, you’ll quickly realize that launching services isn’t enough; you need to connect them securely. The foundation of all networking in AWS is the Virtual Private Cloud (VPC), and the most fundamental building block of a VPC is the subnet. But for many beginners, the question is simple: what is a subnet?
Understanding subnets is the key to unlocking secure and effective cloud architecture. It’s how you separate your public-facing web servers from your private, secure databases. Getting this concept right is non-negotiable for building professional applications on AWS.
This ultimate guide will demystify subnets completely. We will use a simple analogy to explain the concept, break down the critical difference between public and private subnets, and show you how they work together to create a secure network for your cloud resources.
What is a Subnet in Cloud Computing? (Quick Answer)
For those looking for a direct answer, here it is:
A subnet, short for subnetwork, is a logical subdivision of a larger IP network. In AWS, a subnet is a range of IP addresses within your Virtual Private Cloud (VPC). You launch AWS resources, like EC2 instances, into these subnets. The primary purpose of a subnet is to partition your VPC into smaller, manageable segments to improve security and organization.
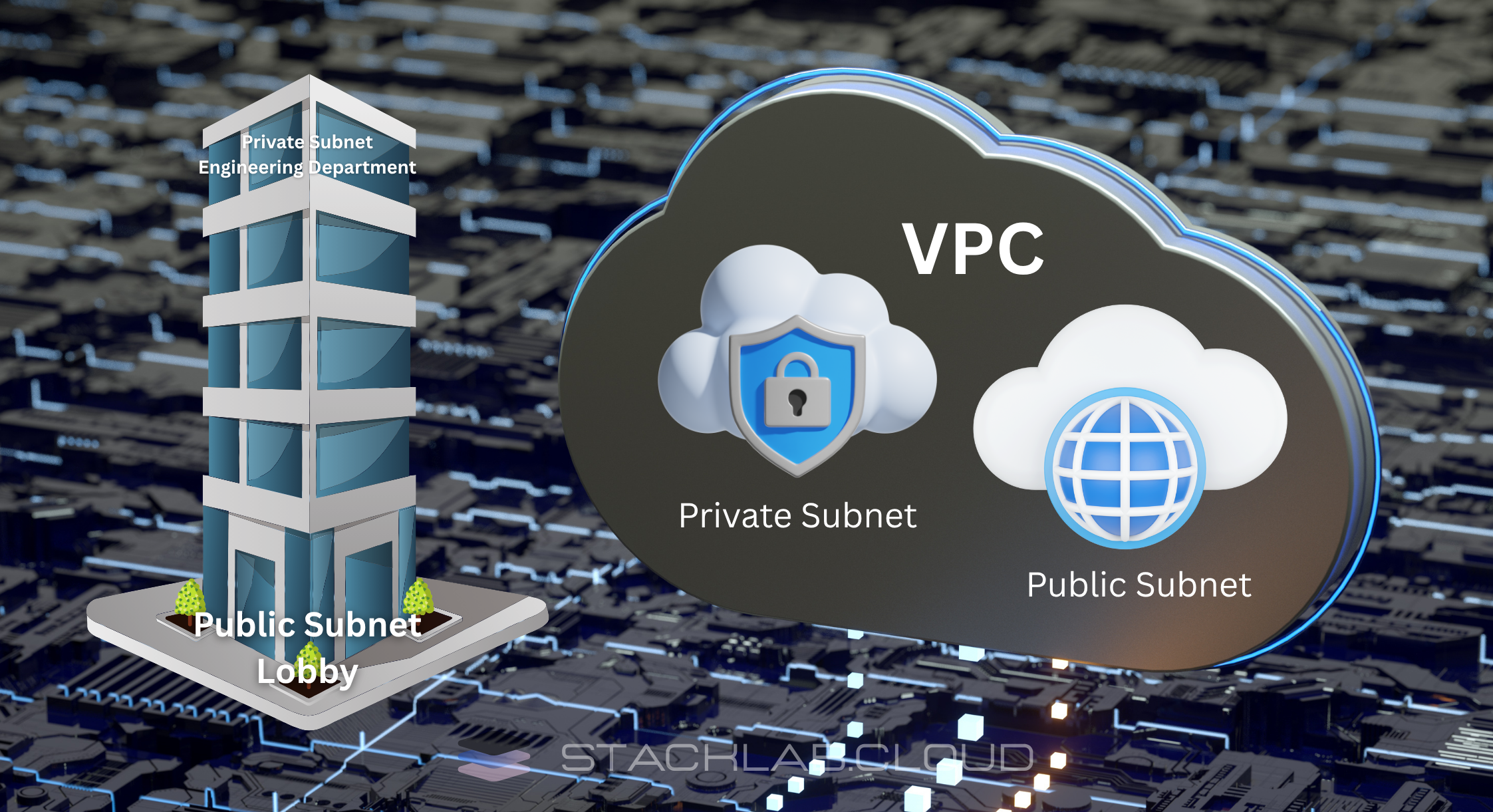
The Best Analogy: The Office Building and Its Departments
To truly understand VPCs and subnets, let’s use a simple real-world analogy: a large, multi-story office building.
- Your VPC (Virtual Private Cloud) is the entire office building. It’s your private, isolated section of the massive AWS cloud. You control who can enter and leave the building itself.
- A Subnet is a specific department or floor within that building. For example, you might designate the 10th floor as the “Sales Department” and the 11th floor as the “Engineering Department.”
You wouldn’t want a random visitor from the lobby to be able to walk directly into the secure Engineering Department where all your secret projects are being built. Instead, you use walls, doors, and key cards to control access between floors. Subnets serve the exact same purpose for your digital resources.
The Core Components of an AWS Subnet
When you create a subnet, you are essentially defining a smaller network inside your main VPC network. This involves a few key concepts.
CIDR Blocks: Defining the IP Address Range
Every VPC has a large range of private IP addresses, defined by a CIDR (Classless Inter-Domain Routing) block, like 10.0.0.0/16. This represents all the possible “office numbers” inside your entire building.
When you create a subnet, you assign it a smaller CIDR block that is a subset of the VPC’s range. For example:
- You could create a “Public Subnet” with the CIDR block
10.0.1.0/24. - You could create a “Private Subnet” with the CIDR block
10.0.2.0/24.
This is like assigning a specific range of office numbers (e.g., 100-199) to a specific department. Any resource launched into that subnet will automatically be assigned a private IP address from that subnet’s range.
Availability Zones: Ensuring High Availability
A critical rule in AWS is that
A subnet must exist entirely within a single Availability Zone (AZ).
An AZ is a distinct physical data center within an AWS Region. They are isolated from each other to prevent failures from spreading.
To build a highly available application, you create multiple subnets in different Availability Zones. For example, you would have a “Public Subnet A” in AZ-1 and a “Public Subnet B” in AZ-2. This way, if the data center in AZ-1 has a problem, your resources in AZ-2 can continue to operate.

Public vs. Private Subnets: The Most Important Distinction
The single most important concept to understand is the difference between a public and a private subnet. What makes a subnet “public” or “private” is not a checkbox you tick; it’s determined entirely by its network routing.
What Makes a Subnet Public?
A subnet is considered public if its traffic is routed to an Internet Gateway (IGW). An Internet Gateway is a VPC component that allows communication between your VPC and the public internet.
Think of the IGW as the main front door of your office building that leads directly to the street (the internet).
- Key Characteristic: The subnet’s associated Route Table has a route (
0.0.0.0/0) that points to the Internet Gateway. - Common Use Case: This is where you place resources that need to be directly accessible from the internet, such as a web server, a public-facing load balancer, or a NAT Gateway.
- IP Addressing: Resources in a public subnet can be assigned a Public IP address in addition to their private IP.
What Makes a Subnet Private?
A subnet is considered private if it does not have a direct route to the Internet Gateway. Traffic from a private subnet cannot reach the internet directly.
Think of this as a secure, windowless server room deep inside your office building. There is no direct door to the outside street.
- Key Characteristic: The subnet’s associated Route Table does not have a route pointing to the Internet Gateway.
- Common Use Case: This is where you place your secure backend resources that should never be exposed to the public internet. This includes your databases, application servers, and any internal processing workloads.
- How it accesses the internet: If a resource in a private subnet needs to access the internet (for example, to download software updates), it must send its traffic through a NAT (Network Address Translation) Gateway that resides in a public subnet.
How Subnets Work with Other AWS Networking Services
Subnets don’t work in isolation. They are part of a larger system of networking components within your VPC.
Route Tables
A Route Table is like a set of GPS directions for network traffic. Each subnet must be associated with a route table, which contains rules that determine where network traffic from the subnet is directed. It’s the route table that defines whether a subnet is public (has a route to the IGW) or private (does not).
Network Access Control Lists (NACLs)
A NACL is like a firewall for your subnet. It acts at the subnet level and controls traffic flowing in and out of one or more subnets. It’s a stateless firewall, meaning you must create rules for both inbound and outbound traffic.
Security Groups
A Security Group is like a firewall for your EC2 instance. It acts at the instance level and controls traffic flowing in and out of a specific instance. It’s a stateful firewall, meaning if you allow inbound traffic, the corresponding outbound traffic is automatically allowed.
You use both NACLs and Security Groups together to create a layered security defense for your applications.
Conclusion: The Foundation of Secure Architecture
So, what is a subnet? It is the fundamental tool you use to partition your private cloud network (VPC) into logical, secure segments. By creating public subnets for your web-facing resources and private subnets for your backend databases and application servers, you are implementing a core security best practice.
Understanding how to design a VPC with a proper subnet architecture is the first step towards building applications on AWS that are not just powerful and scalable, but also secure and resilient.
FAQ: AWS Subnets
1. Can a resource in a public subnet talk to a resource in a private subnet?
Yes. By default, all subnets within the same VPC can communicate with each other using their private IP addresses, regardless of whether they are public or private. You can control this traffic using Security Groups and Network ACLs.
2. What is a “Default VPC”?
When you create a new AWS account, AWS automatically creates a “Default VPC” in each region for you. This VPC comes with pre-configured public subnets in each Availability Zone, an Internet Gateway, and a default route table. It’s designed to make it easy for beginners to launch resources quickly without needing to configure networking first.
3. How many IP addresses are in a subnet?
The number of available IP addresses is determined by the CIDR block size. For example, a `/24` CIDR block has 256 total IP addresses. However, AWS reserves 5 of these addresses for its own networking purposes, so a `/24` subnet gives you 251 usable IP addresses for your resources.











